
 Chip Services
Chip Services

 Products
Products
- Automotive and Industrial control
- Information Security
- Edge Computing& Network Communication
Products

 Resources
Resources

 Language
Language
Overview:
C*Core’s Trusted Cryptography Modules(TCM) CCT01 and CCT02 are designed based on the CUni360S and CCM3310S-H chips respectively. The interfaces comply with the "GM/T 0012-2020 Trusted Computing - Trusted cryptography Module Interface Specification", and the chips comply with GM/T 0028-2014 "Security Technical Requirements for Cryptography Modules" and GM/T0008-2012 "Cryptography Test Criteria for Security IC ". The chips are designed based on the 32-bit security CPU CS0 with independent intellectual property rights, distinguished by low power consumption, high performance, multifunction and high security level.
The chips are equipped with high-level secure hardware algorithm coprocessors that support national commercial cryptographic algorithm and international standard algorithms. At the same time, the chips include multiple interface types to meet the requirements of trusted computing modules to the greatest extent. The chips support industrial-grade temperature range -40℃ to 85℃for harsh industrial environments.
Parameters
| Model | CCT01 | CCT02 |
Processor | C*Core 32-bit CS0 | C*Core 32-bit CS0 |
Frequency | 80MHz | 100MHz |
Communication Protocol | SPI | SPI |
Operating Voltage | 1.62V~5.5V | 1.62V~3.6V |
Operating Voltage | SM2/SM3/SM4 | SM2/SM3/SM4 |
Package Type
| Model | CCT01 | CCT02 |
Type | QFN76 | QFN40 |
Dimension | 9mm*9mm*0.75mm | 5mm*5mm*0.55mm |
Appearance:

Solution:
The trusted computing solution launched by C*Core (Tianjin) meets the Level 1 to Level 4 requirements of GB/T 22239-2019 "Information security technology -- Baseline for classified protection of cybersecurity"
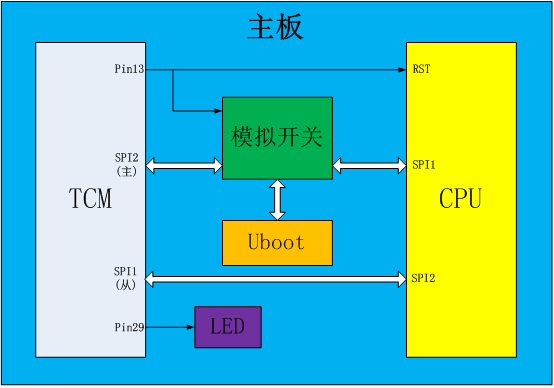
Embedded Trusted Platform Solution Diagram
The embedded trusted platform solution launched by C*Core (Tianjin) has the following advantages:
1.The Core key’s memory is implemented within the trusted root and cannot be exported, and protected data leaving the host environment cannot be decrypted.
2.By gradually measuring trust, a trust chain is established from the host's firmware to the OS and then to applications, resisting known/unknown malicious code attacks.
3.Based on trusted computing technology, it ensures the credibility of system processes combined with the trusted root, preventing identity spoofing and theft.
4.Through access control technology, it ensures that system resource access and process execution are within the scope of security policy control, preventing unauthorized operations and unauthorized resource modification.
5.It builds a host kernel-level trust chain to perform integrity measurements on all loaded and running program code, ensuring that all program code and configurations running on the system are in a trusted state.
6.It detects and prevents the execution of malicious code hidden within legitimate programs, achieving active immunity against known/unknown malicious code.
7.It supports whitelisting settings for host applications, scripts, plugins, etc. The system enforces whitelisting, allowing only approved programs to run, thus preventing unauthorized software, malware, and viruses from executing.